Are your devices spying on you? Australia's very small step to make the Internet of Things safer
- Written by Kayleen Manwaring, Senior Lecturer, School of Taxation & Business Law, UNSW
From internet-connected televisions, toys, fridges, ovens, security cameras, door locks, fitness trackers and lights, the so-called “Internet of Things” (IoT) promises to revolutionise our homes.
But it also threatens to increase our vulnerability to malicious acts. Security flaws in IoT devices are common[1]. Hackers can exploit those vulnerabilities to take control[2] of devices, steal or change data[3], and spy on us[4].
In recognition of these risks, the Australian government has introduced a new code of practice[5] to encourage manufacturers to make IoT devices more secure. The code provides guidance on secure passwords, the need for security patches, the protection and deletion of consumers’ personal data and the reporting of vulnerabilities, among other things.
The problem is the code is voluntary. Experiences elsewhere, such as the United Kingdom, suggest a voluntary code will be insufficient to deliver the protections consumers need.
Indeed it might even increase risks, by lulling consumers into a false sense of security about the safety of the devices they buy.
Read more: Explainer: the Internet of Things[6]
Many IoT devices are insecure
IoT devices designed for consumers are generally less secure than conventional computers.
In 2017 the Australian Communications Consumer Action Network commissioned researchers from the University of New South Wales to test the security of 20 household appliances[7] capable of being connected and controlled via wi-fi.
These included a smart TV, portable speaker, voice assistant, printer, sleep monitor, digital photo frame, bathroom scales, light bulb, power switch, smoke alarm and Hello Barbie talking doll.
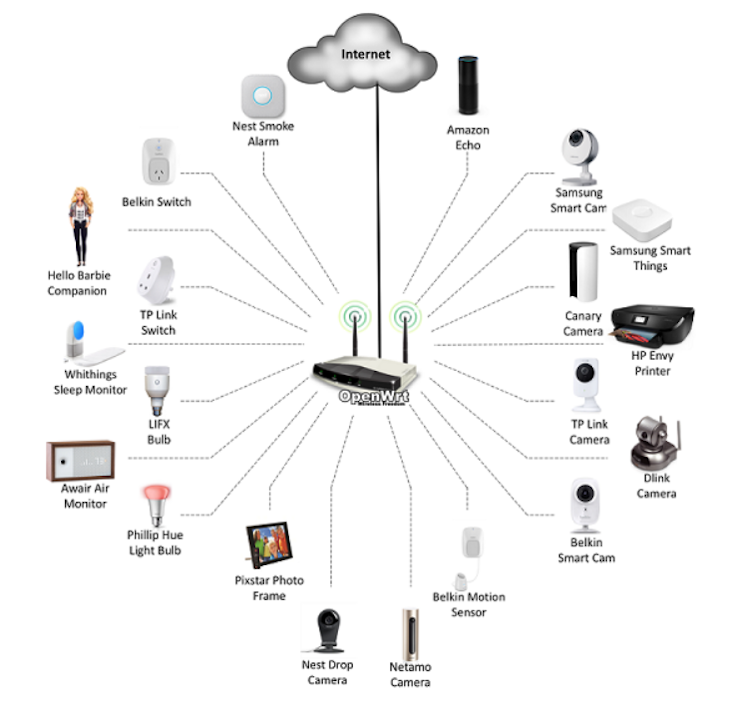 Devices tested by UNSW researchers for the Australian Communications Consumer Action Network.
Inside Job: Security and privacy threats for smart-home IoT devices, 2017, CC BY-NC[8][9]
Devices tested by UNSW researchers for the Australian Communications Consumer Action Network.
Inside Job: Security and privacy threats for smart-home IoT devices, 2017, CC BY-NC[8][9]
While some devices (including the Barbie) were found to be relatively secure in terms of confidentiality, all had some form of security flaw. Many “allowed potentially serious safety and security breaches”.
What this could potentially mean is that someone could, for example, hack into a household’s wi-fi network and collect data from IoT devices. It might be as simple as knowing when lights are switched on to determine when a home can be burgled. Someone with more malicious intent could turn on your oven[10] while shutting down smoke alarms and other sensors.
Risks to consumers, and society
Factors leading to poor security in IoT devices[11] include manufacturers’ desires to minimise componentry and keep costs down. Many makers of consumer goods also have little experience with cyber-security issues.
Allied with the fact many consumers aren’t technologically savvy[12] enough to appreciate the risks and protect themselves, this creates the prospect of IoT devices being exploited.
Read more: The privacy paradox: we claim we care about our data, so why don't our actions match?[13]
On a personal level, you could be spied on and harassed[14]. Personal pictures or information could be exposed to the world[15], or used to extort you.
On a societal level, IoT devices can be hijacked[16] and used collectively to shut down services and networks. Even compromising one device may enable connected infrastructure to be hacked. This is a rising concern as more people connect to workplace networks[17] from home.
 Many consumers don’t fully appreciate the security risks from IoT devices.
Shutterstock
Many consumers don’t fully appreciate the security risks from IoT devices.
Shutterstock
Voluntary codes of practice
In recognition of these threats, IoT security “good practice” guidelines have been proposed by standards bodies such as the US National Institute of Standards and Technology[18], the European Telecommunications Standards Institute[19] and the Internet Engineering Task Force[20]. But these guidelines are based on voluntary action by manufacturers.
The UK government has already concluded[21] the voluntary code of conduct it established in 2018[22] isn’t working.
Britain’s Minister for Digital Infrastructure, Matt Warman, said in July:
Despite widespread adoption of the guidelines in the Code of Practice for Consumer Internet of Things Security[23], both in the UK and overseas, change has not been swift enough, with poor security still commonplace.
The UK is now moving[24] to impose a mandatory code, with laws requiring manufacturers to deliver reasonable security features in any device that can connect to the internet.
A case for co-regulation
There is little reason to believe Australia’s voluntary code of practice will prove any more effective than in the UK.
A better option would have been a “co-regulatory[25]” approach. Co-regulation mixes aspects of industry self-regulation with both government regulation and strong community input[26]. It includes laws that create incentives for compliance (and disincentives against non-compliance) and regulatory oversight by an independent (and well-resourced) watchdog.
The Australia government has, at least, described its new code of practice as “a first step” to improving the security of IoT devices.
Let’s hope so. If the UK experience is anything to go by, its next steps will include dumping a voluntary code for something with a greater chance of delivering the safety and security consumers – and society – need.
References
- ^ are common (papers.ssrn.com)
- ^ control (www.theguardian.com)
- ^ steal or change data (www.forbes.com)
- ^ spy on us (www.forbes.com)
- ^ code of practice (www.homeaffairs.gov.au)
- ^ Explainer: the Internet of Things (theconversation.com)
- ^ household appliances (accan.org.au)
- ^ Inside Job: Security and privacy threats for smart-home IoT devices, 2017 (accan.org.au)
- ^ CC BY-NC (creativecommons.org)
- ^ turn on your oven (phys.org)
- ^ poor security in IoT devices (www5.austlii.edu.au)
- ^ aren’t technologically savvy (accan.org.au)
- ^ The privacy paradox: we claim we care about our data, so why don't our actions match? (theconversation.com)
- ^ spied on and harassed (www.vice.com)
- ^ exposed to the world (www.ftc.gov)
- ^ hijacked (elie.net)
- ^ workplace networks (www.iotworldtoday.com)
- ^ US National Institute of Standards and Technology (www.nist.gov)
- ^ European Telecommunications Standards Institute (www.etsi.org)
- ^ Internet Engineering Task Force (datatracker.ietf.org)
- ^ concluded (www.gov.uk)
- ^ established in 2018 (assets.publishing.service.gov.uk)
- ^ Code of Practice for Consumer Internet of Things Security (www.gov.uk)
- ^ moving (www.gov.uk)
- ^ co-regulatory (rogerclarke.com)
- ^ community input (rogerclarke.com)
Authors: Kayleen Manwaring, Senior Lecturer, School of Taxation & Business Law, UNSW